DNS Records: The Mysterious Scrolls That Control the Internet😶🌫️

Ah, DNS records! Those magical little text files that decide where your website lives, how emails are delivered, and whether hackers can ruin your day. You’ve probably heard of them, or maybe you’ve ignored them—until something breaks. Let’s unravel these mysterious internet scrolls before they make you pull your hair out.
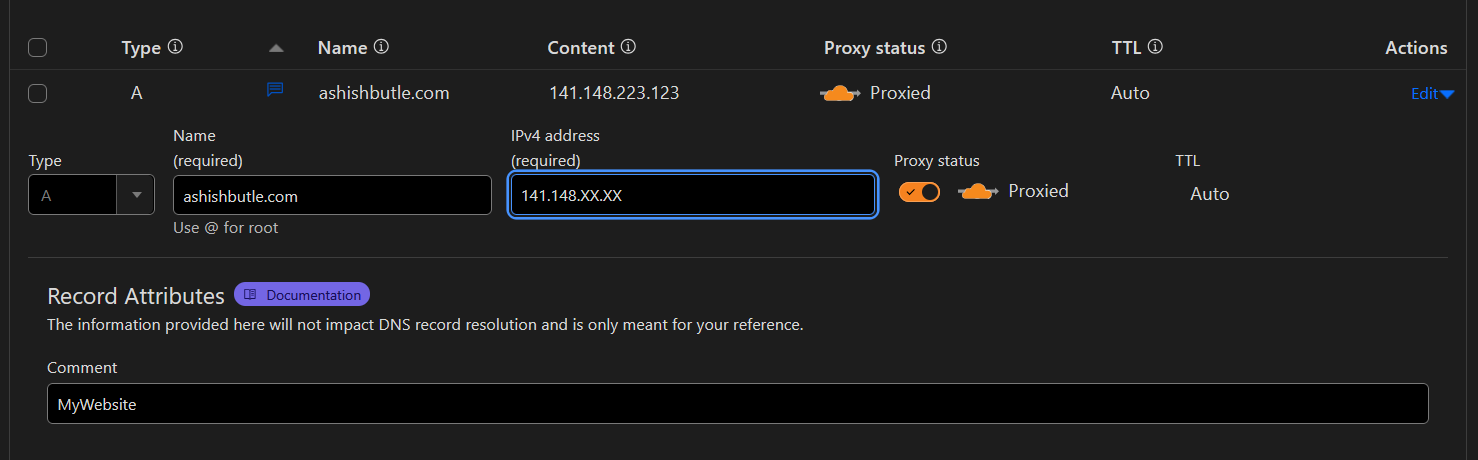
1) A Record (A for "Ah, This is the Address!
This one is the VIP of DNS records. It translates your fancy domain name (like Ashishbutle.com) into an IP address (155.155.155.x, or whatever tech gobbledygook it has). Without it, your website is as lost as a tourist without Google Maps.
2) CNAME (Because One Name is Never Enough!)
This is for when you're too lazy to remember multiple IP addresses. Instead of assigning an IP, you point one domain to another domain. Think of it as internet-level copy-pasting.

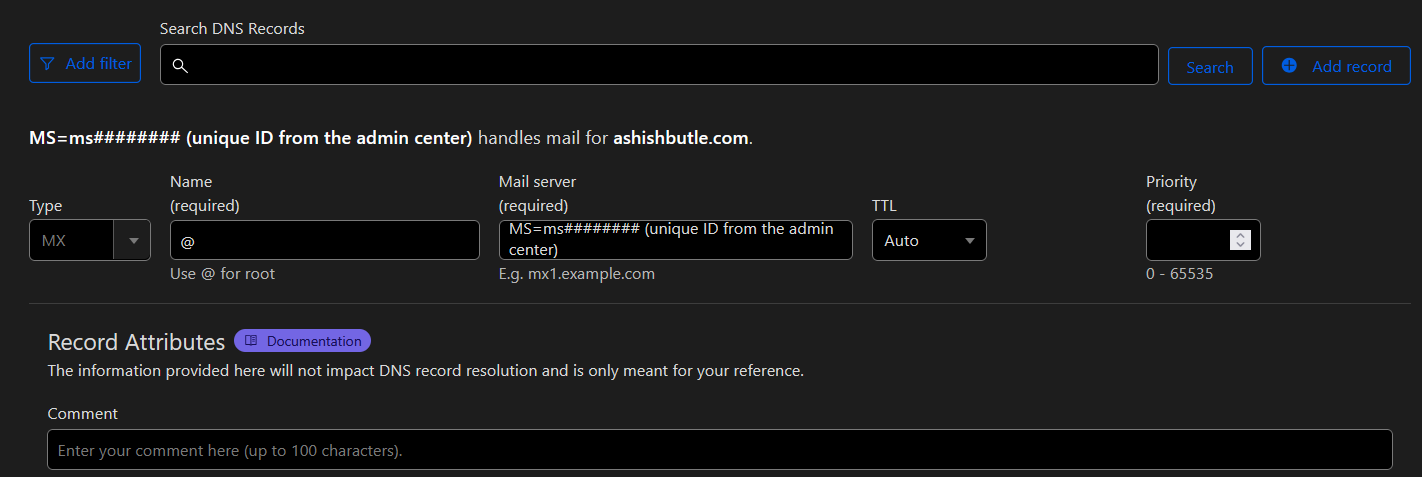
3) MX Records (Mail X-periments)
These decide where your emails go. If you mess them up, expect your emails to vanish into the abyss, never to be seen again.
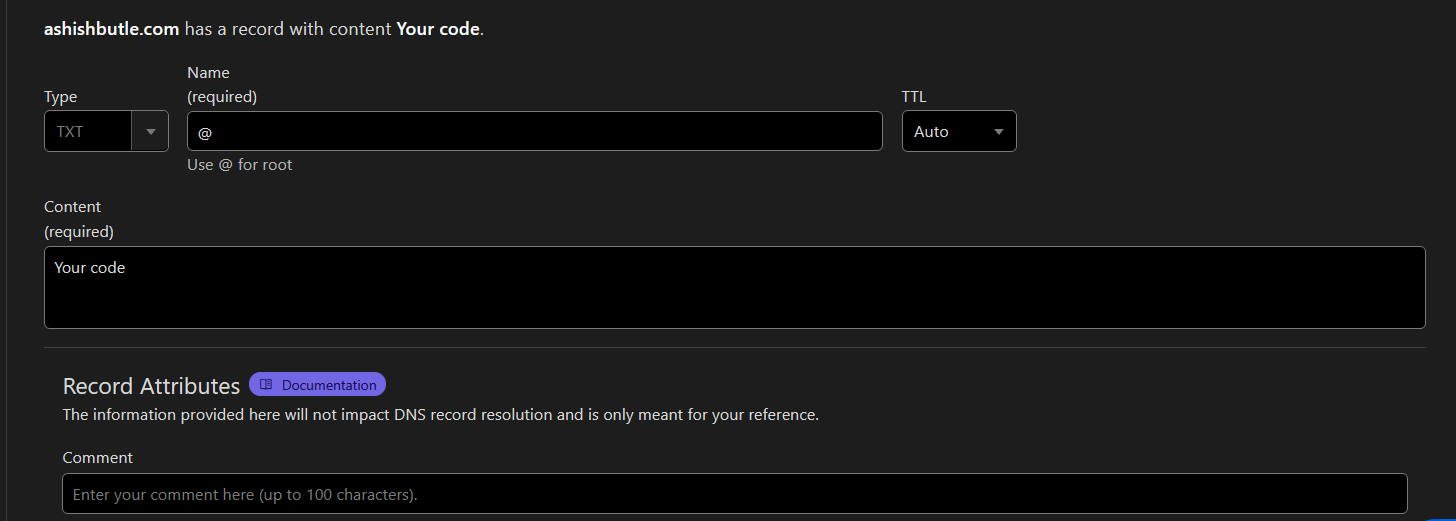
4) TXT Records (Where Security and Nonsense Collide)
TXT records let you store random text, but mostly they exist so security features like SPF, DKIM, and DMARC can pretend to protect your emails from spammers.
5) NS Records (Because Someone Has to be in Charge!)
These tell the world which name servers are responsible for your domain. If they go wrong, your entire website becomes an urban legend—people swear it exists, but no one can actually find it.
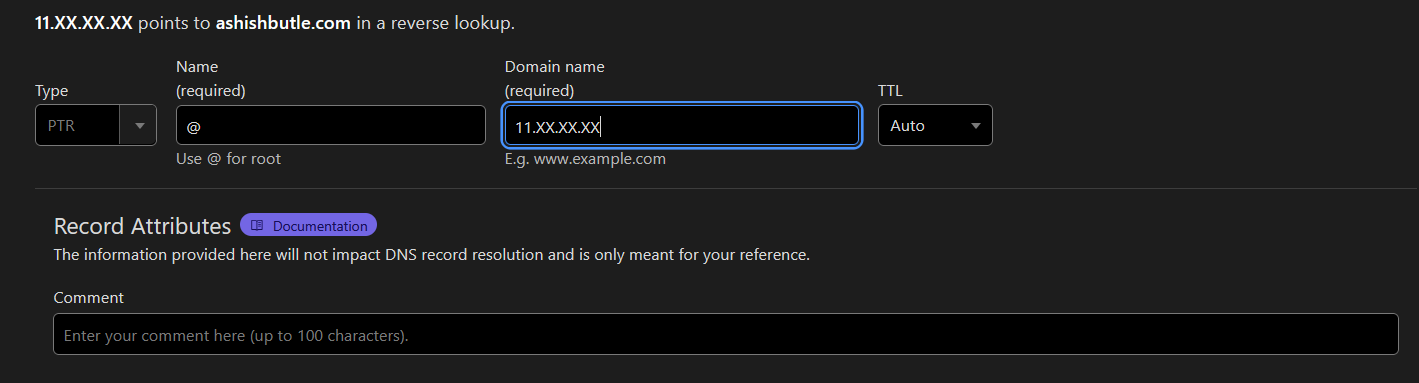
6) PTR Records (Reverse DNS, Because Normal DNS Was Too Boring)
These do the opposite of A records—turn an IP address into a domain name. They’re mostly useful for email servers, but only if you enjoy making your IT team cry when they’re missing.
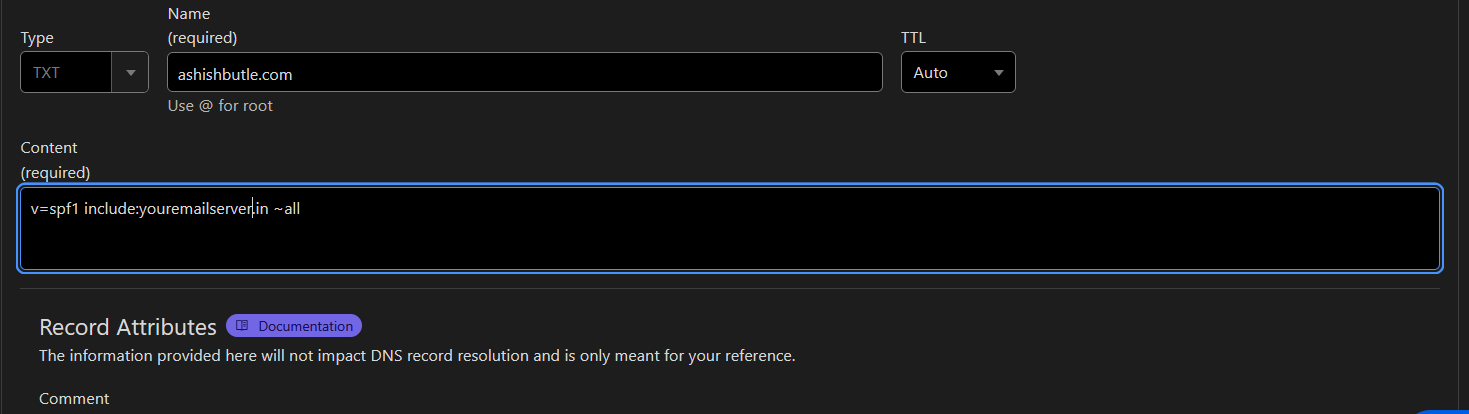
7) SPF (Sender Policy Framework: The Email ID Checker)
SPF is like a VIP list for email senders. It tells email servers which IP addresses are allowed to send emails on behalf of your domain. If an email comes from an IP not on the list, SPF squints at it suspiciously and might toss it into spam or reject it.
🧐 How it works:
- You add a TXT record in your DNS with a list of approved email-sending IPs.
- Email servers check if an email comes from one of those IPs.
- If the sender isn’t on the list, SPF yawns, shrugs, and lets the email through anyway—unless DMARC steps in (we’ll get to that).
⚠️ Common SPF Mistakes:
- Forgetting to update it when you change email providers (enjoy your missing emails!).
- Adding too many “include” statements—because there’s a limit, and DNS doesn’t care about your feelings.
- Thinking SPF alone is enough (spoiler alert: It’s not).
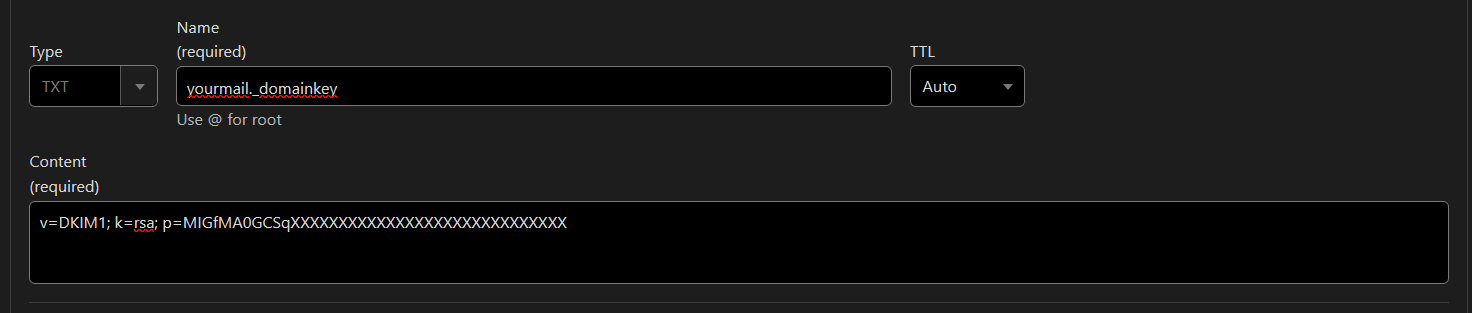
8) DKIM (DomainKeys Identified Mail: The Email Signature Expert)
DKIM is your email’s notary public—it signs your emails with a cryptographic signature, proving they weren’t tampered with during delivery.
📜 How it works:
- Your email server attaches a secret signature to your email.
- The receiving server checks your DNS for the public key to verify the signature.
- If the signature doesn’t match, DKIM says, “Nah, this looks shady”, and the email might be rejected or marked as spam.
✍️ Why DKIM Matters:
- Prevents email spoofing (a hacker pretending to be you).
- Ensures your emails aren’t modified in transit (because who doesn’t love a hacker editing your emails?).
- Boosts your email deliverability (because Google and Microsoft trust DKIM-signed emails more).
🚨 Common DKIM Fails:
- Forgetting to enable DKIM for your domain (great job, now anyone can spoof your emails!).
- Having multiple DKIM records that confuse email servers (because why make things simple?).
- Using weak cryptographic keys (might as well just hand out your password).
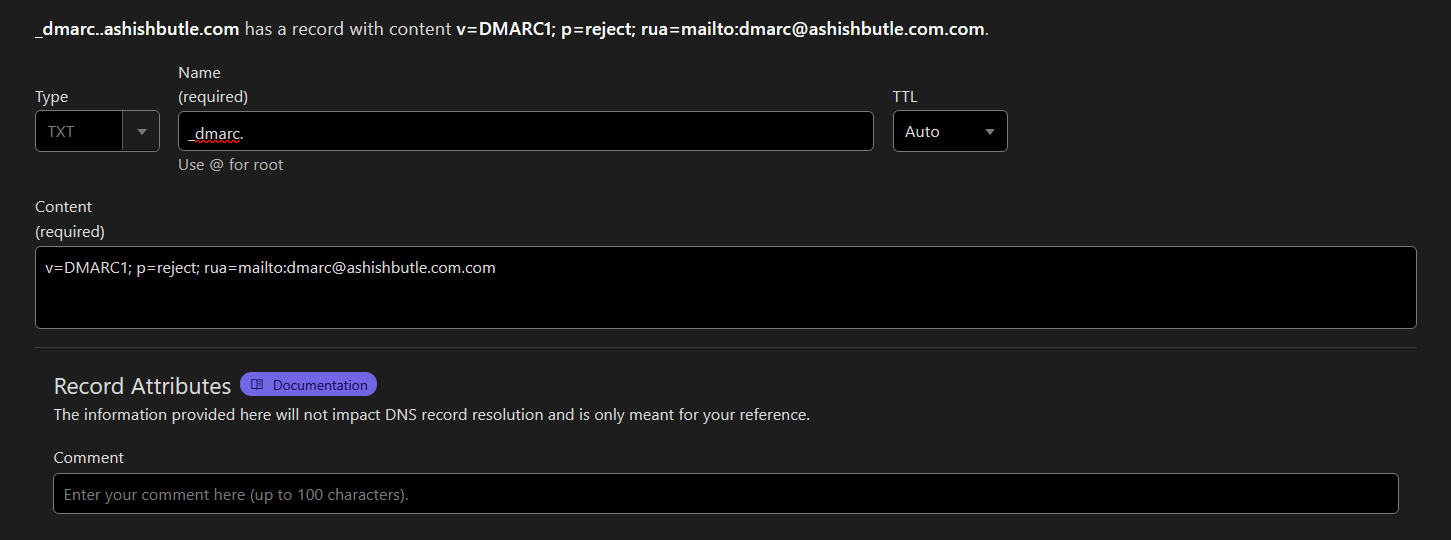
9) DMARC (Domain-based Message Authentication, Reporting & Conformance: The Email Enforcer)
DMARC is the boss of email security. It uses SPF and DKIM to decide what to do with suspicious emails. Think of it as a bouncer standing at the door of your inbox, checking IDs and kicking out fakes.
👮 How it works:
- It checks SPF and DKIM results for incoming emails.
- If an email fails authentication, DMARC follows the policy you set:
none= “Eh, whatever, let it through.”quarantine= “Throw it in spam, just in case.”reject= “GTFO.”
- It sends reports about who’s trying to spoof your domain (good luck deciphering those XML files, though).
🛑 DMARC Mistakes to Avoid:
- Setting
p=noneand thinking you're protected (that’s like leaving your door open but having a “No burglars allowed” sign). - Going straight to
p=rejectwithout testing first—because yes, blocking your own emails is a thing. - Ignoring DMARC reports (why collect data if you’re never going to read it?).
Final Thoughts: Be Nice to Your DNS Records
Your DNS records control how people find your website, send you emails, and generally interact with your digital empire. If you mess them up, expect chaos, frustration, and probably a few angry emails (which, ironically, you won’t receive because, well… you broke your MX record).
So, the next time you think DNS is “just a bunch of settings,” remember: it’s the only thing standing between you and complete internet oblivion.
